I log a warning to also keep track of possibly probing requests.
Useless, from time to time i look into server logs - there are TONS of probing requests, on ALL servers that i own (including ones spun up minutes ago) from lots of different IPs. That’s too typical to react to any of these requests (otherwise you’ll be on high alert 24/7)
P.S. Just do good practices - no passwords for ssh (keys only), no external access to db, redis etc, read and use guides for building sql queries to prevent injections etc etc etc - and sleep well ;). Otherwise you’re screwed anyway
2 Likes
Update:
I got 4 honeypot servers running. 3 of them completely new and only reachable via their IP. Another is is a bit older and has an unused domain assigned to it, in addition to the IP.
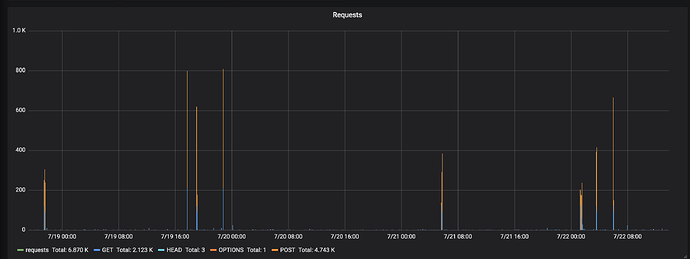
Over the last 3 - 4 days, they received almost 7000 requests.
They received 8 big crawling attacks, originating from 8 different IPs. Most of the IPs are reachable and most of them contain Chinese content. Even though those IPs host different content, their “attack” looks familiar. It starts with a bunch of GET requests, than a hell lot of POST requests and then some GET requests again. Mostly aimed at PHPMyAdmin and PHP code injection.
I also logged all query params and POST data but haven’t done any sorting/grouping on them.
I find this very interesting. Those crawling attacks request a whole lot of paths. Each attack created around 800 requests but all with unique paths (within these 800 requests).
2 Likes
I just quickly put this together today:
Once I added proper documentation besides the README, I will publish it to hex and create a separate thread for it here on the forum.
2 Likes