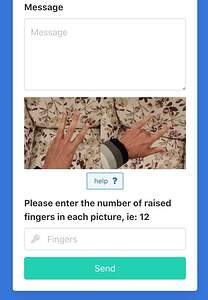
So far
It has been out in the wild for a couple of days but had 0 spam incoming and now time to reap the benefits
Setup and context
- field is named as “fingers”, throws bots off, don’t know how to treat the field name
- It is marked as required on HTML5 form as well as on the server validation which happens in the controller or Ecto right now.
- It is a number field on HTML5, so only integer numbers can be entered given the browser supports it
- A human is expected to enter numbers into it
I have been logging stuff on the “failed cases”
don’t worry omitting password and email fields before logging
Failed Registration from 5.166.201.102
%{"email" => "***@gmail.com", "fingers" => "", "name" => "Susanteete", "password" => "***"}
Failed Contact from 170.254.230.186
%{"email" => "***@edlen.com", "fingers" => "rdHoGzYqkDZLgVc", "message" => "mWAhJiaHvrMLSlR", "subject" => "YQJxLAFTXWkVl"}
Failed Registration from 170.254.230.186
%{"email" => "***@edlen.com", "fingers" => "NMFbSguTeYn", "name" => "ocJLmzwV", "password" => "***"}
You can check the reputation of IPs from this open community awesomeness (which I use to mass ban 20k bots via my firewall, god knows how much logs I would get if I hadn’t already)
https://www.abuseipdb.com/check/170.254.230.186
It is definitely a harmful spam bot.
Armed with these bits of information we could do the following.
Taking it to the next level
When the verification fails, don’t just disregard it, but pass the answer and given answer into the library analysis section. Could be a different supervisor tree or even offline, cron process.
Hoomannn vs Makina
- Is it empty? It can’t be empty for an actual user with a “text/html” browser
- Is it the required string length? Asked for 2 images how many did we receive?
- Does it contain non-numeric characters? It can’t or shouldn’t be for an actual user on html browser.
Ok matches total weight is higher than the threshold, very likely a bot but could be a human dicking around:
- Verify the reputation and confidence with abuseipdb api
- Send the report to abuseipdb, because even dicking around is abuse and should be reported. If it’s a genuine user then it will expire after a while without given no any other reports incoming.
Not enough confidence or evidence:
- log and move on
Enough confidence and evidence:
- Ban the IP via OS, network firewalls (ufw, iptables, ipset, WAF etc)
- Preferably via a small driver package for each flavour
what do you people think?