Hi everyone.
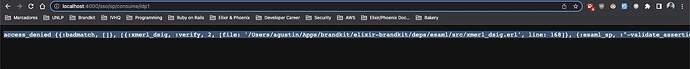
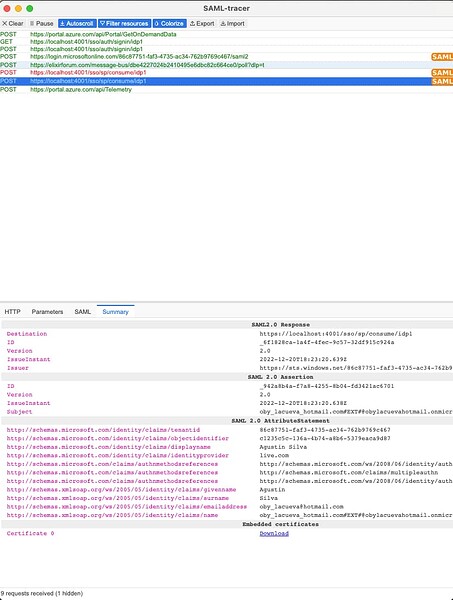
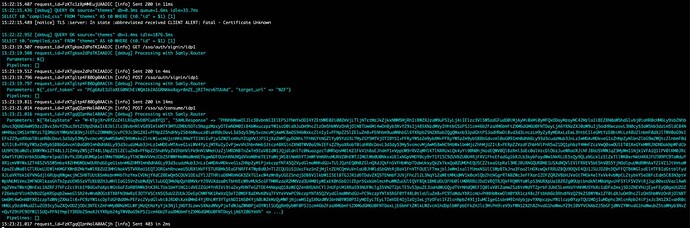
I’m trying to add Azure AD SSO to an app I’m working on and when I try to start the login process I’m getting the following error:
Just in case, it’s my first time working with SAML, Azure AD and SSO.
My config/dev.exs file has the bare minimum settings in order to make it work asap and then I’ll add the optional stuff:
config :samly, Samly.Provider,
idp_id_from: :path_segment,
service_providers: [
%{
id: "sp1",
entity_id: "idp1",
# certfile: "priv/cert/samly_sp.pem",
# keyfile: "priv/cert/samly_sp.pem"
}
],
identity_providers: [
%{
id: "idp1",
sp_id: "sp1",
base_url: "http://localhost:4000/sso",
metadata_file: "idps-metadata/idp1-metadata.xml",
pre_session_create_pipeline: MySamlyPipeline,
sign_requests: false,
sign_metadata: false
}
]
The MySamlyPipeline plug is the same as the one shown in the docs:
defmodule MySamlyPipeline do
use Plug.Builder
alias Samly.{Assertion}
plug :compute_attributes
plug :jit_provision_user
def compute_attributes(conn, _opts) do
assertion = conn.private[:samly_assertion]
IO.inspect(assertion, label: "ASSERTION")
# This assertion has the idp_id
# %Assertion{idp_id: idp_id} = assertion
first_name = Map.get(assertion.attributes, "first_name")
last_name = Map.get(assertion.attributes, "last_name")
computed = %{"full_name" => "#{first_name} #{last_name}"}
assertion = %Assertion{assertion | computed: computed}
conn
|> put_private(:samly_assertion, assertion)
# If you have an error condition:
# conn
# |> send_resp(404, "attribute mapping failed")
# |> halt()
end
def jit_provision_user(conn, _opts) do
# your user creation here ...
conn
end
end
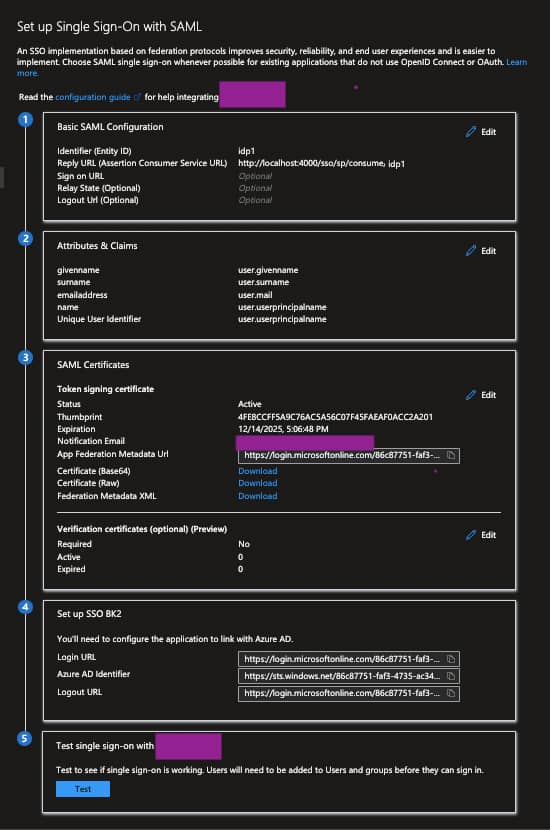
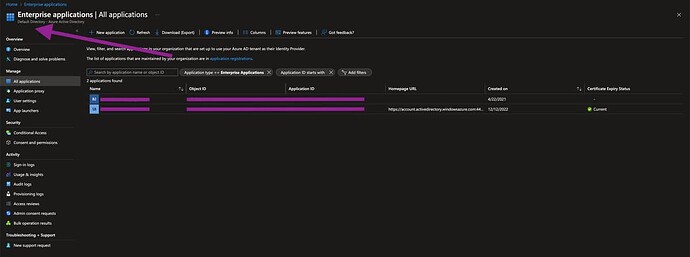
Finally, my Enterprise Application in Azure has the following configs:
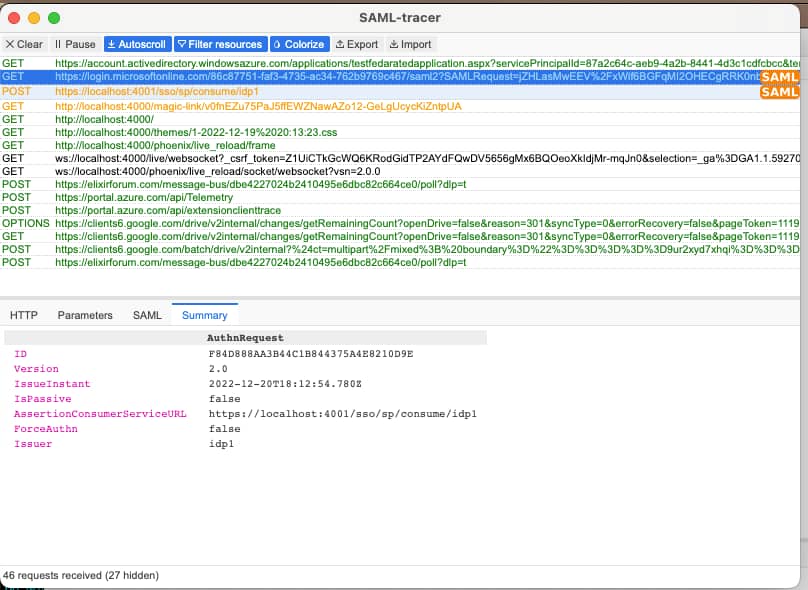
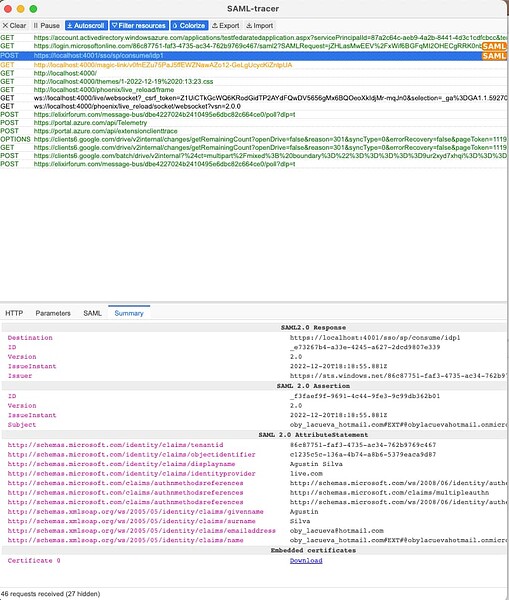
I’ve read the docs a few times and there are no posts about how to set up Azure AD using Samly. Also, I’ve inspected the code from the samly_howto but I couldn’t solve it neither.
I’m not sure what I’m doing wrong. I’m pretty sure it has to be some misconfiguration.
Any help would be appreciated ![]()
Cheers.