Pre-info:
webserver : Cowboy only, not using nginx
My certs is from Let’s Encrypt (certbot)
Debian 8
Generated dh-param.pem file using openssl
1/
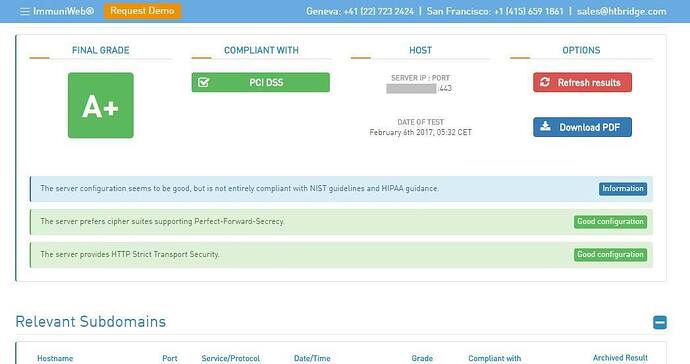
SSL Tester: https://www.htbridge.com/ssl
Right now, it can’t fulfill the “elliptic curves” criteria.
“The server supports elliptic curves that are considered weak.”
(currently I get A-, compared to capped at B- for the “do nothing” config)
Q. How do I pass in these values as in Erlang -- ssl
to my Phoenix config? (let’s say I am using dev.exs for this)
I am getting
[warn] Transport option {:eccs,
["sect571r1", "sect571k1", "secp521r1", "brainpoolP512r1", "sect409k1",
"sect409r1", "brainpoolP384r1", "secp384r1", "sect283k1", "sect283r1",
"brainpoolP256r1", "secp256k1", "secp256r1", "sect239k1", "sect233k1",
"sect233r1", "secp224k1", "secp224r1"]} unknown or invalid.
OR
[warn] Transport option {:honor_ecc_order, true} unknown or invalid.
[warn] Transport option {:eccs,
[:sect571r1, :sect571k1, :secp521r1, :brainpoolP512r1, :sect409k1, :sect409r1,
:brainpoolP384r1, :secp384r1, :sect283k1, :sect283r1, :brainpoolP256r1,
:secp256k1, :secp256r1, :sect239k1, :sect233k1, :sect233r1, :secp224k1,
:secp224r1]} unknown or invalid.
for the keys eccs and honor_ecc_order .
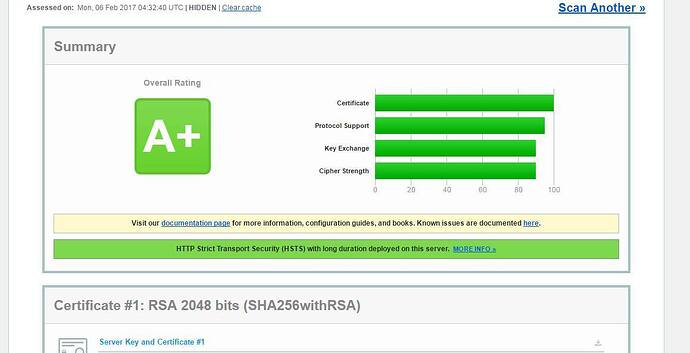
2/
SSL Tester: SSL Server Test (Powered by Qualys SSL Labs)
I am getting A- (improved from the basic grade of B for ‘do nothing’ config)
“The server does not support Forward Secrecy with the reference browsers. Grade reduced to A-.”
Q. Could anyone give a clue on how to resolve that?
In short:
Although I do already get A- now, but I would like to know how to pass those options that I mentioned in order to get the satisfying “full compliance as per recommended” result. (For reference, I have achieved this before in my other tech stack’s webserver.)
The main point for me is to learn how to use Phoenix’s config file to pass the options I mentioned(through cowboy?) all the way to ssl options as stated as available in Erlang -- ssl
 (congrats!)
(congrats!)


 Thanks again for sharing your experience!
Thanks again for sharing your experience! 



















