Hi everyone here, many thanks for your help, and for your interest! ![]()
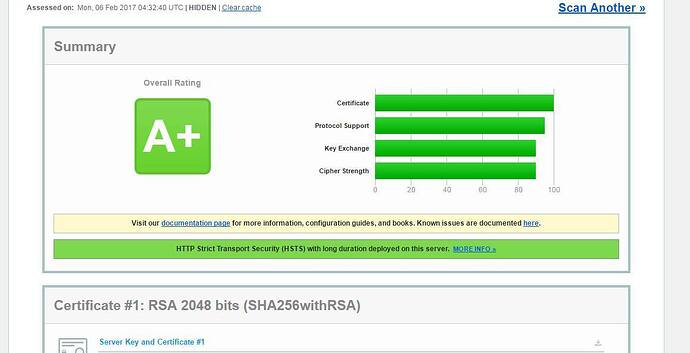
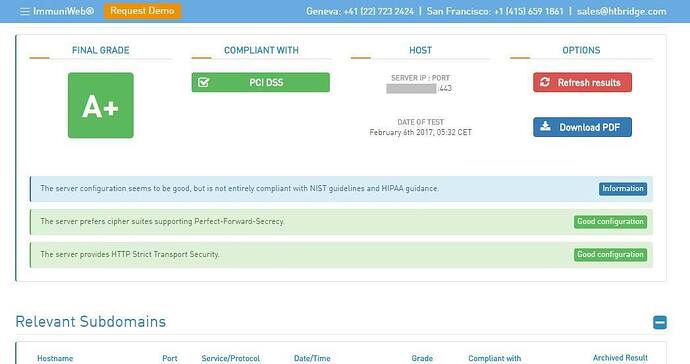
So, now I am Proud Asian Dad, as it is possible to get A+ for BOTH ssllabs and htbridge’s ssl tests:
This:
and this:
Ok, let me see if I can provide a step by step here as an article might take too long.
1/ Basically, googling for “let’s encrypt” may eventually bring you to “certbot” which following the instructions here, you ssh into your server and follow step by step.
This obtains free SSL certs and auto-renews them using cron jobs.
A word here, the scripts by default run as root, so you may want to explore further at this stage “automated but not as root”
But if you want to just get everything running quickly to try out, you can just follow the original instructions.
2/
Next is you put the settings in your config file (e.g. dev.exs or another)
I just put the settings here that get you the A+ result above…
Also left in the commented-out options, to show that I found that they were not necessary (but others could tell more about these if they know more about them)
config :hello_phoenix, HelloPhoenix.Endpoint,
http: [port: 80],
#force_ssl: [rewrite_on: [:x_forwarded_proto]],
url: [host: "asdf.qwer.com"],
force_ssl: [],
https: [port: 443,
otp_app: :hello_phoenix,
keyfile: "/PATH/TO/asdf.qwer.com/privkey.pem",
certfile: "/PATH/TO/asdf.qwer.com/cert.pem",
cacertfile: "/PATH/TO/asdf.qwer.com/chain.pem",
versions: [:"tlsv1.2", :"tlsv1.1", :"tlsv1"],
ciphers: ~w(
ECDHE-ECDSA-AES256-GCM-SHA384
ECDHE-ECDSA-AES256-SHA384
ECDHE-ECDSA-AES128-GCM-SHA256
ECDHE-ECDSA-AES128-SHA256
ECDHE-ECDSA-AES256-SHA
ECDHE-ECDSA-AES128-SHA
ECDHE-RSA-AES256-GCM-SHA384
ECDHE-RSA-AES256-SHA384
ECDHE-RSA-AES128-GCM-SHA256
ECDHE-RSA-AES128-SHA256
ECDHE-RSA-AES256-SHA
ECDHE-RSA-AES128-SHA
ECDH-ECDSA-AES256-GCM-SHA384
ECDH-ECDSA-AES256-SHA384
ECDH-ECDSA-AES128-GCM-SHA256
ECDH-ECDSA-AES128-SHA256
DHE-RSA-AES256-GCM-SHA384
DHE-RSA-AES256-SHA256
DHE-DSS-AES256-GCM-SHA384
DHE-DSS-AES256-SHA256
DHE-RSA-AES256-SHA
DHE-DSS-AES256-SHA
DHE-DSS-AES128-GCM-SHA256
DHE-RSA-AES128-GCM-SHA256
DHE-RSA-AES128-SHA256
DHE-DSS-AES128-SHA256
DHE-RSA-AES128-SHA
DHE-DSS-AES128-SHA
AES128-GCM-SHA256
AES128-SHA
DES-CBC3-SHA
)c,
dhfile: "/PATH/TO/projects/hello_phoenix/dh-params.pem",
secure_renegotiate: true,
reuse_sessions: true,
honor_cipher_order: true,
# http://erlang.org/doc/man/ssl.html#type-ssloption
### honor_ecc_order: true,
client_renegotiation: false,
eccs: [
:sect571r1, :sect571k1, :secp521r1, :brainpoolP512r1, :sect409k1,
:sect409r1, :brainpoolP384r1, :secp384r1, :sect283k1, :sect283r1,
:brainpoolP256r1, :secp256k1, :secp256r1, :sect239k1, :sect233k1,
:sect233r1, :secp224k1, :secp224r1
],
],
3/ As @voltone pointed out, if you used a wrong format for the ciphers, they will be silently ignored and the default suites used, that gets you A- or something else. If you use the one as shown here, they will be correct.
4/ So now running the tests on your server would give the same result.
‘OSCP Stapling’ item is not supported by the webserver, but that’s not quite important and there’s nothing you can do about it as well.
5/ I did not happen to try out (plug!) @voltone’s cipher_suites | Hex since I only got to know of it so late, but I expect that you will get the same good result in one step rather than doing it by hand as I did (looking up and copying the openssl aliases) ![]() If you do try it, do let us know how it works!
If you do try it, do let us know how it works!