I have the following routes
get "/locations", LocationsController, :show
get "/locations/add", LocationsController, :add
post "/locations/add", LocationsController, :create
get "/units", LocationsController, :show_units
get "/unit/add", LocationsController, :add_units
post "/unit/add", LocationsController, :create_units
get "/products", ProductsController, :show
get "/product/add", ProductsController, :add
post "/products/add", ProductsController, :create_product
get "/barcodes", ProductsController, :show_barcodes
get "/barcode/add", ProductsController, :add_barcode
post "/barcode/add", ProductsController, :create_barcode
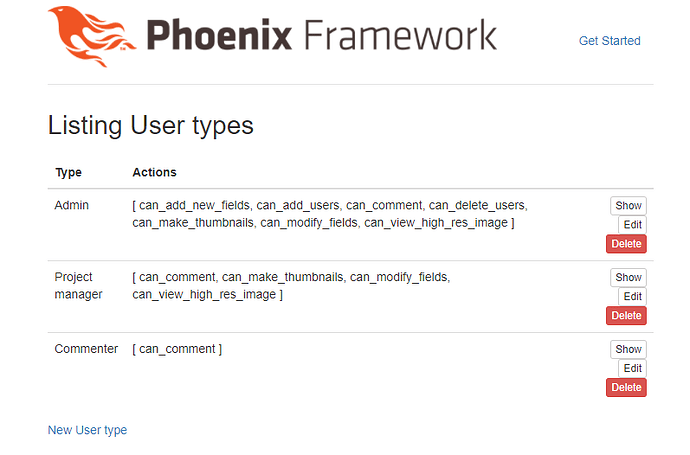
I have three permission groups(admin can add more permission group)
can_admin_location
can_admin_products
can_admin_barcode
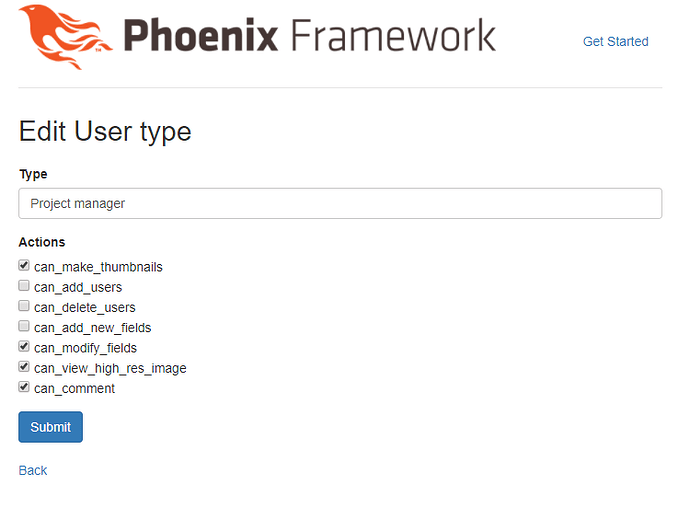
For example, You can see the below image to understand more what i am trying to achieve
I want to restrict route access based on permission given
For example if the below permission
can_admin_barcode (can use only below routes)
get "/barcodes", ProductsController, :show_barcodes
get "/barcode/add", ProductsController, :add_barcode
post "/barcode/add", ProductsController, :create_barcode
Then admin can change the user access level for this permission group
can_admin_barcode (can only view barcodes and only the below route will be accessible by this user)
get "/barcodes", ProductsController, :show_barcodes
Routes blocking must happen dynamically
I am storing current logged in user permission in session. I believe i can achieve this Route restriction using plugs.
Can someone share some insight on how to achieve this or any example. Your help is greatly appreciated