@cmkarlsson
Sorry am just 1 yr old at this elixir erlang game 
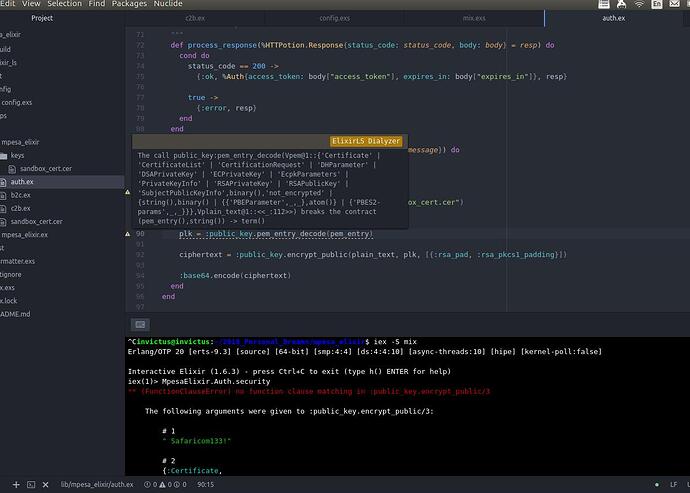
Here is :term am getting from pem_entry_decode
{:Certificate,
{:TBSCertificate, :v3, 240747201527587228894948,
{:AlgorithmIdentifier, {1, 2, 840, 113549, 1, 1, 11}, <<5, 0>>},
{:rdnSequence,
[
[
{:AttributeTypeAndValue, {0, 9, 2342, 19200300, 100, 1, 25},
<<22, 3, 110, 101, 116>>}
],
[
{:AttributeTypeAndValue, {0, 9, 2342, 19200300, 100, 1, 25},
<<22, 9, 115, 97, 102, 97, 114, 105, 99, 111, 109>>}
],
[
{:AttributeTypeAndValue, {2, 5, 4, 3},
<<19, 32, 83, 97, 102, 97, 114, 105, 99, 111, 109, 32, 73, 110, 116,
101, 114, 110, 97, 108, 32, 73, 115, 115, 117, 105, 110, 103, 32, 67,
65, 32, 48, 50>>}
]
]}, {:Validity, {:utcTime, '141112071245Z'}, {:utcTime, '161111071245Z'}},
{:rdnSequence,
[
[{:AttributeTypeAndValue, {2, 5, 4, 6}, <<19, 2, 75, 69>>}],
[
{:AttributeTypeAndValue, {2, 5, 4, 8},
<<19, 7, 78, 97, 105, 114, 111, 98, 105>>}
],
[
{:AttributeTypeAndValue, {2, 5, 4, 7},
<<19, 7, 78, 97, 105, 114, 111, 98, 105>>}
],
[
{:AttributeTypeAndValue, {2, 5, 4, 10},
<<19, 7, 78, 97, 105, 114, 111, 98, 105>>}
],
[
{:AttributeTypeAndValue, {2, 5, 4, 11},
<<19, 10, 84, 101, 99, 104, 110, 111, 108, 111, 103, 121>>}
],
[
{:AttributeTypeAndValue, {2, 5, 4, 3},
<<19, 24, 97, 112, 105, 99, 114, 121, 112, 116, 46, 115, 97, 102, 97,
114, 105, 99, 111, 109, 46, 99, 111, 46, 107, 101>>}
]
]},
{:SubjectPublicKeyInfo,
{:AlgorithmIdentifier, {1, 2, 840, 113549, 1, 1, 1}, <<5, 0>>},
<<48, 130, 1, 10, 2, 130, 1, 1, 0, 168, 183, 5, 117, 87, 21, 236, 119, 68,
58, 139, 108, 52, 186, 12, 62, 16, 251, 224, 37, 245, 122, 60, 220, 129,
243, 110, 136, ...>>}, :asn1_NOVALUE, :asn1_NOVALUE,
[
{:Extension, {2, 5, 29, 14}, false,
<<4, 20, 193, 71, 196, 248, 216, 6, 157, 213, 131, 55, 112, 242, 86, 159,
130, 2, 33, 117, 102, 72>>},
{:Extension, {2, 5, 29, 35}, false,
<<48, 22, 128, 20, 235, 50, 212, 79, 126, 96, 154, 58, 152, 32, 99, 186,
13, 94, 190, 232, 121, 78, 213, 36>>},
{:Extension, {2, 5, 29, 31}, false,
<<48, 130, 1, 46, 48, 130, 1, 42, 160, 130, 1, 38, 160, 130, 1, 34, 134,
129, 214, 108, 100, 97, 112, 58, 47, 47, 47, 67, 78, 61, ...>>},
{:Extension, {1, 3, 6, 1, 5, 5, 7, 1, 1}, false,
<<48, 129, 249, 48, 129, 201, 6, 8, 43, 6, 1, 5, 5, 7, 48, 2, 134, 129,
188, 108, 100, 97, 112, 58, 47, 47, 47, 67, 78, ...>>},
{:Extension, {2, 5, 29, 15}, false, <<3, 2, 5, 160>>},
{:Extension, {1, 3, 6, 1, 4, 1, 311, 21, 7}, false,
<<48, 46, 6, 38, 43, 6, 1, 4, 1, 130, 55, 21, 8, 135, 207, 140, 86, 132,
194, 196, 3, 133, 233, 133, 54, 132, 222, ...>>},
{:Extension, {2, 5, 29, 37}, false,
<<48, 20, 6, 8, 43, 6, 1, 5, 5, 7, 3, 2, 6, 8, 43, 6, 1, 5, 5, 7, 3, 1>>},
{:Extension, {1, 3, 6, 1, 4, 1, 311, 21, 10}, false,
<<48, 24, 48, 10, 6, 8, 43, 6, 1, 5, 5, 7, 3, 2, 48, 10, 6, 8, 43, 6, 1, 5,
5, 7, 3, ...>>}
]}, {:AlgorithmIdentifier, {1, 2, 840, 113549, 1, 1, 11}, <<5, 0>>},
<<76, 20, 169, 103, 113, 128, 200, 211, 172, 226, 71, 70, 116, 254, 183, 169,
180, 130, 81, 8, 202, 62, 174, 170, 63, 113, 75, 143, 40, 201, 137, 9, 141,
236, 95, 17, 71, 179, 152, 165, 53, 122, 60, 97, 171, 224, ...>>}
I can`t see any public key attribute anywhere.