Long story short, I have a JavaScript frontend client and two backends: one in Python (for login/signup) and one in Phoenix (used only for websockets).
My Python backend sets an HTTP-only JWT token and successfully handles login and signup when users interact with the JavaScript frontend client.
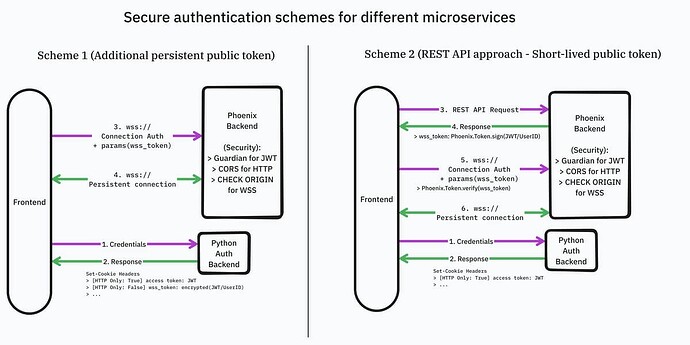
Once a user has logged in, they should be able to connect to the Phoenix backend’s channels with the cookies previously set. I’ve managed to make Phoenix + Guardian work for JWT HTTP secure authentication, but I’m facing difficulties with websockets. As far as I know, sending an HTTP-only cookie to the Phoenix backend for websockets is not possible due to security reasons (browsers allow cross-origin connections that bypass CORS).
So, how can I authenticate my users from the frontend who have already logged in (with jwt token cookie http only set to true) and need to connect to Phoenix websocket channels?
Here are the solutions I’ve been considering:
- On the Python backend, when a user logs in or signs up, I set another cookie with an encrypted JWT and make it HTTP-only false. Then, I can access this token on the frontend’s socket connection to the Phoenix backend and verify & decode it.
- Create a REST API in the Python backend for the encrypted JWT, which I can use for websocket connections to the Phoenix backend for verification.
P.S: Still, I’m hesitant about encrypting the JWT and storing it in cookies with HTTP-only set to false. This approach leaves room for XSS vulnerabilities since the token can be accessed directly from document.cookies and potentially stolen for connecting to the Phoenix websocket backend as a victim