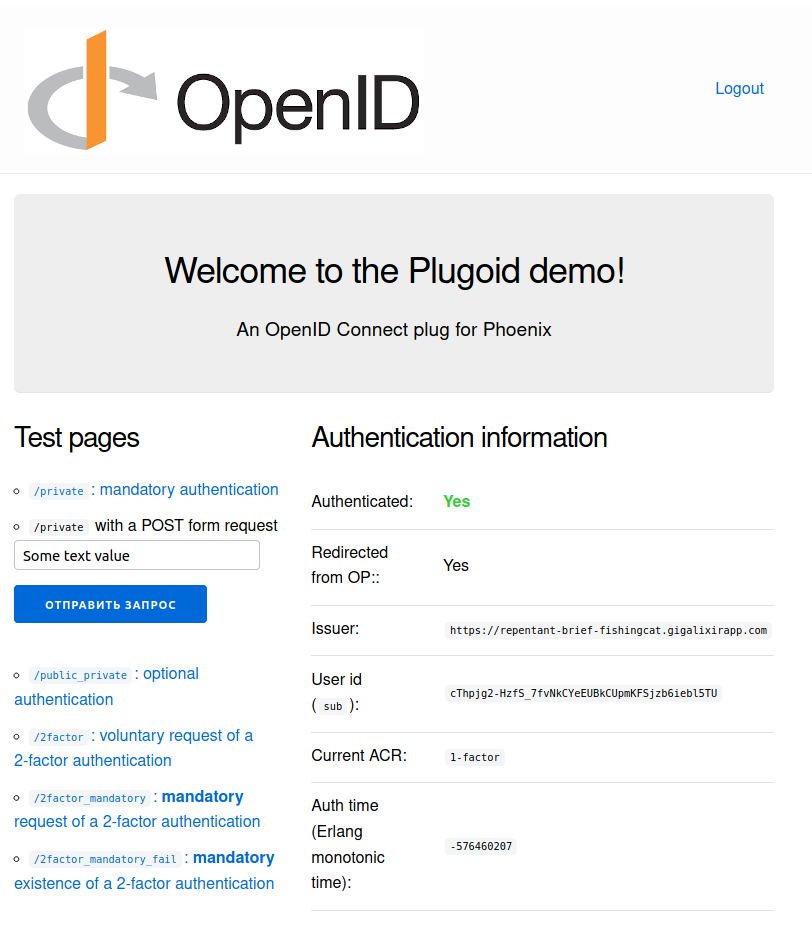
I’m glad to release the first version of Plugoid, an OpenID Connect library for Phoenix.
This library can be useful if you delegate authentication completely to an OpenID Connect Provider.
Example configuration:
defmodule MyApp.Router do
use MyApp, :router
use Plugoid.RedirectURI
pipeline :oidc_auth do
plug Plugoid,
issuer: "https://repentant-brief-fishingcat.gigalixirapp.com",
client_id: "client1",
client_config: MyApp.OpenIDConnect.Client
end
scope "/private", MyApp do
pipe_through :browser
pipe_through :oidc_auth
get "/", PageController, :index
post "/", PageController, :index
end
end
More information here:
Although it’s version 0.1.0, it has a quite comprehensive support of the standard (see the README for more information). Any feedback is welcome on the issue tracker!
You can try it out with the https://github.com/tanguilp/plugoid_demo application.
For those working with OAuth2 or OpenID Connect, a few additional libraries that were needed to build Plugoid could prove useful:
-
Oauth2MetadataUpdater: retrieves OAuth2 and OpenID Connect metadata -
JWKSURIUpdater: JWKS key downloader -
OAuth2TokenManager: manages OAuth2 tokens and OpenID Connect claims and ID tokens -
JOSEUtils: Convenience functions to work with JOSE (JSON Object Signing and Encryption) on top of theJOSElibrary -
TeslaOAuth2ClientAuth: Tesla middlewares for OAuth2 and OpenID Connect client authentication
Also I’ve seen that some people were looking for some project to contribute too - for those, feel free to look at the issue trackers of these libraries and contact me if you’re interested on working on an issue.
Have a good evening!